Overview
This paper discusses the interworking of untrusted non-3GPP networks and the 5G Core Network (5GCN) using the non-3GPP Interworking Function (N3IWF). The N3IWF acts as a gateway for the 5GCN with support for N2 and N3 interface towards the 5GCN. Additionally, N3IWF provides a secure connection for the UE accessing the 5GCN over non-3GPP access network with support for IPsec between the UE and the N3IWF. The paper describes the architecture of untrusted non-3GPP network interworking with 5G core, including the interfaces, protocols and the procedures used, and QoS support. Specifically, the paper details the control plane (CP) functionalities including registration and PDU session establishment and user plane (UP) functionalities including QoS for untrusted non-3GPP access and in the N3IWF. The current 3GPP specification specifies support for only Wireless LAN (Wi-Fi) Access Network (WLAN) as the non-3GPP access network; hence, the same is considered for the untrusted non-3GPP access network in this paper.
Need
Untrusted WLANs include public hotspots, home Wi-Fi, corporate Wi-Fi etc. that are not controlled by the mobile network operator. However, by enabling convergence to a single 5GCN providing various IP based services untrusted non-3GPP/WLAN can supplement the 3GPP access networks to address the following
Evolution
Figure 1 shows the evolution of architecture for untrusted WLAN interworking with 3GPP mobile networks. Access to the 3GPP network prior to the 4G/5G from an untrusted WLAN is provided through a Wireless Access Gateway (WAG) and a Packet Data Gateway (PDG). The PDG includes a Tunnel Termination Gateway (TTG) and a subset of GGSN functionality working with TTG. The AAA server is used to authenticate the UEs over untrusted WLAN using EAP-AKA/EAP-SIM authentication via WAG. The CP signalling between TTG and GGSN uses GTPC protocol and establishes PDP contexts for user sessions. For each UE session established an IPsec tunnel terminates at the TTG and a corresponding GTPU tunnel is established to the GGSN.
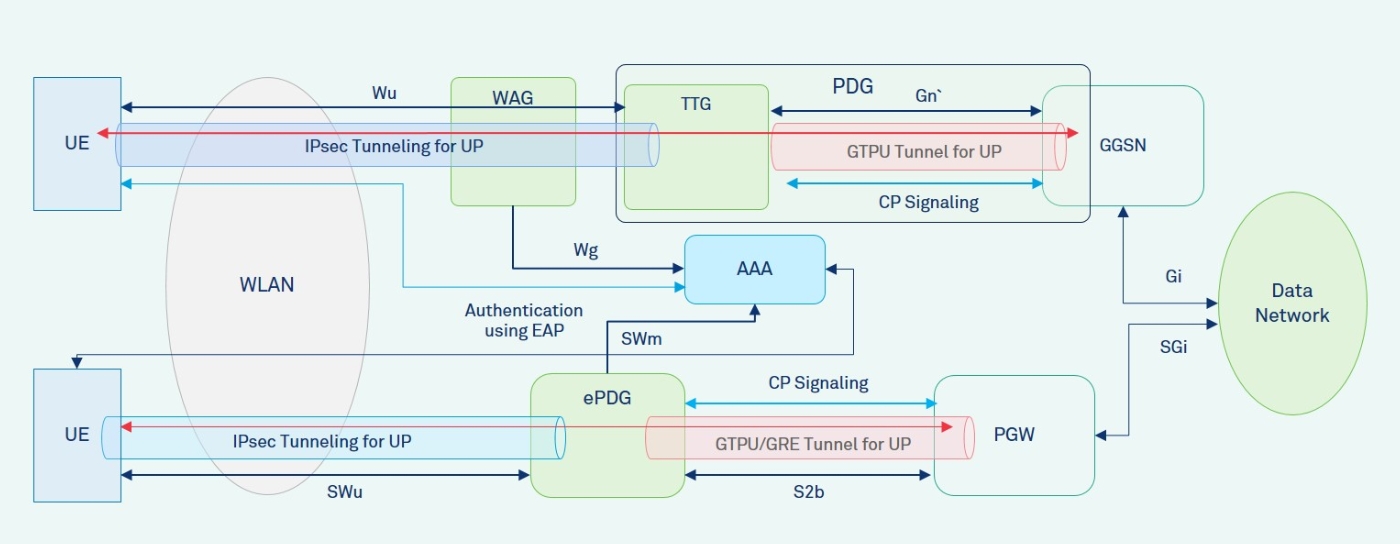
Figure 1: Evolution of Architecture for Untrusted WLAN Interworking
Access to the 4G network from an untrusted WLAN is provided through the evolved Packet Data Gateway (ePDG) using EAP-AKA/EAP-AKA` authentication with AAA server. The CP signalling between ePDG and PGW uses GTPC/PMIP protocol and establishes bearers for user sessions. For each UE session established over untrusted WLAN an IPsec tunnel terminates at the ePDG and a corresponding GTPU/GRE tunnel is established to the PGW. The Dual Stack MIPv6 protocol may also be used to establish IPsec between UE and ePDG for CP signalling and establish tunnel between UE and PGW for UP.
Architecture
The network architecture for untrusted WLAN access interworking with 5GCN is shown in Figure 2. A UE accessing the 5GCN through an untrusted WLAN shall support NAS signalling and shall initially register and authenticate with the 5GCN using the N3IWF. Unlike the earlier architectures for untrusted WLAN the registration and authentication procedures are similar to 3GPP access where the AMF is used to register the UE and the AUSF is used to authenticate the UE using EAP-AKA`/5G-AKA authentication. Before the end of registration procedure an IPsec Security Association (SA) is setup between the UE and N3IWF for securing the NAS mobility and session management messages. The UE shall establish PDU sessions using the IPsec signalling SA using the NAS session management messages with the SMF via the AMF. During the establishment of a PDU session, the N3IWF shall set up IPsec Child SAs with the UE for various QoS flows corresponding to the PDU session and a GTPU tunnel with the UPF. The transfer of UL and DL data packets between the UE and data network uses the secure IPsec tunnel(s) between UE and N3IWF and the GTPU tunnel between N3IWF and UPF. The details of the architecture are further discussed in the following sections.
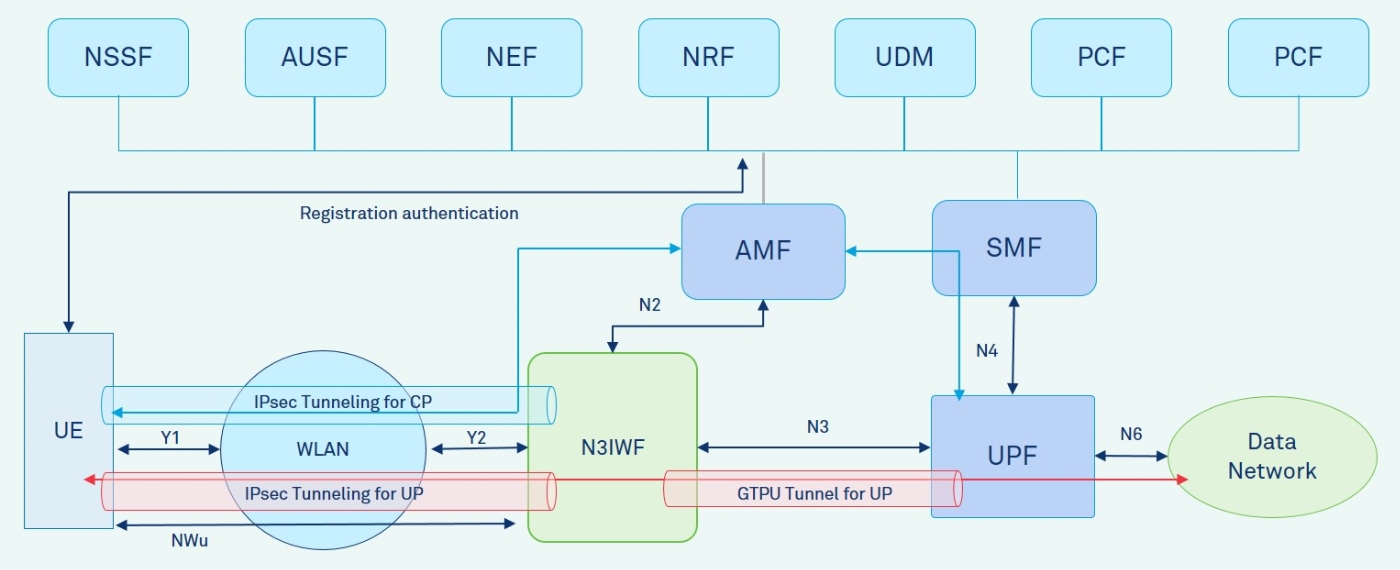
Figure 2: Architecture for Untrusted WLAN Interworking with 5GCN
Interfaces
The untrusted WLAN interworking with 5GCN supports the following interfaces:
Protocols
This section specifies the CP and (UP) protocol stacks used in UE, WLAN AP, N3IWF, AMF and UPF for accessing the 5GCN from an untrusted WLAN.
Control plane protocol stacks
The (CP) protocol stacks provide the protocols used in UE, WLAN, N3IWF and AMF for the following:
Protocol stack for initial registration and authentication
The CP protocol stack for initial access to 5GCN is shown in Figure 3. To register to the 5GCN, the UE first needs to select and connect to a WLAN over the Y1 interface using the WLAN protocol. Once the UE is configured with a local IP address from the selected WLAN, the UE shall select the N3IWF and shall initiate the IKEv2 SA establishment procedure with the N3IWF over the NWu interface using the IKEv2 protocol. After the IKEv2 SA establishment, the N3IWF starts the EAP-5G procedure with the UE which initiates the registration and authentication procedure using the NAS protocol with the AMF over N1 interface. The NAS messages are transported using the EAP-5G/IKEv2 between the N3IWF and UE over NWu interface and using the NGAP/SCTP protocol between the N3IWF and AMF over the N2 interface.
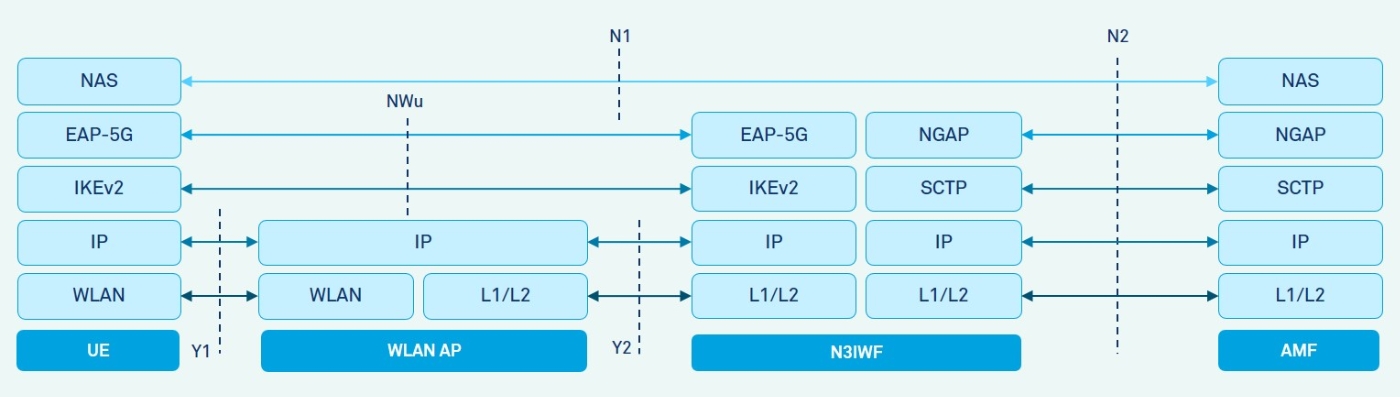
Figure 3: Control Plane before Signalling IPsec SA
Protocol stack for NAS mobility and session management
At the end of the registration procedure, a signalling IPsec SA is established between the UE and the N3IWF after which the UE establishes a TCP connection with the N3IWF for transport of NAS mobility and session management messages over the inner IP layer and the signalling IPsec SA. IPsec tunnel mode is employed for the signalling SA to protect and encrypt the original IP signalling packets and the port numbers used for communications of such IP packets. The CP protocol stack after signalling IPsec SA is shown in Figure 4.

Figure 4: Control Plane after Signalling IPsec SA
Large NAS messages may be fragmented by the inner IP layer or by TCP. UDP protocol may be used between the UE and N3IWF to enable NAT traversal for IKEv2 and IPsec traffic.
Protocol stack for establishing user plane
During the session establishment procedure, the N3IWF initiates the establishment of the IPsec Child SAs with the UE using the IKEv2 protocol as showin in Figure 5 for tunneling the UP traffic.
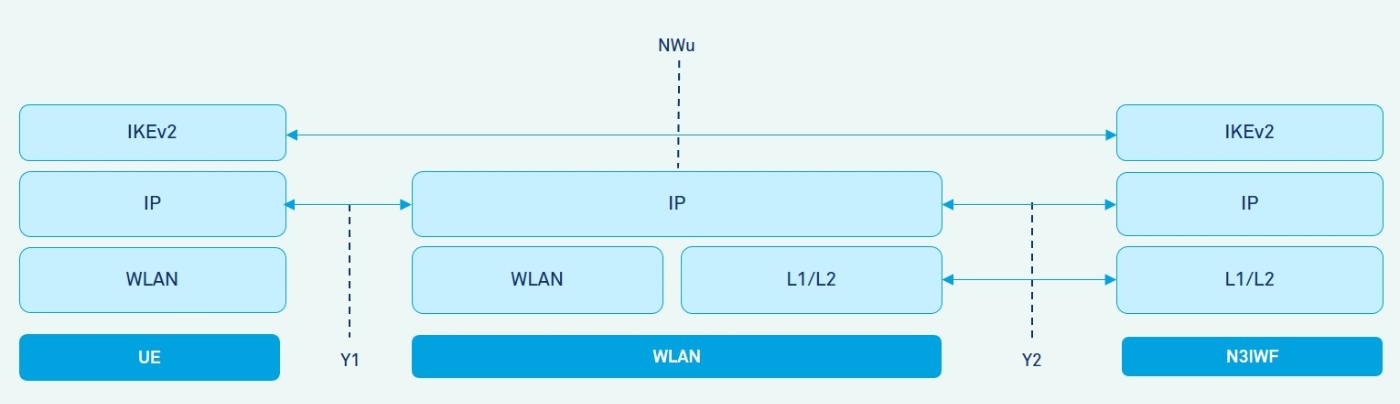
Figure 5: Control Plane for Establishing User Plane
User plane protocol stack
The UP protocol stack shown in Figure 6 involves the protocols used in UE, WLAN, N3IWF and UPF for transferring the UP traffic between the UE and data network. IPsec tunnel mode is employed for the established Child SAs to protect and encrypt the original IP user data packets and the port numbers used for communications of such IP packets.
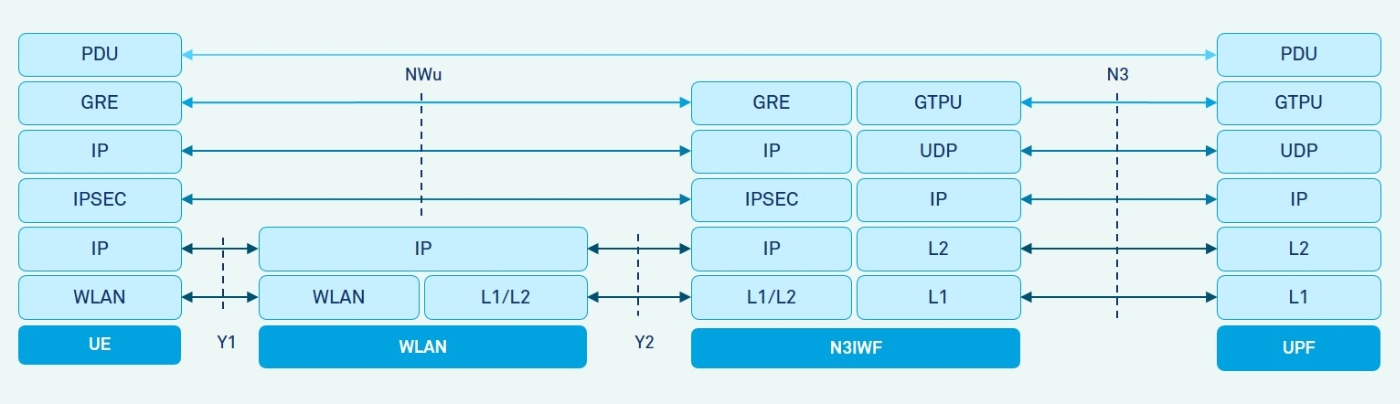
Figure 6: User Plane Protocol Stack
N3IWF Functionalities
This section specifies the CP and UP functionalities of N3IWF for accessing the 5GCN from an untrusted WLAN.
Control plane functionalities
The N3IWF supports the following CP functionalities:
User plane functionalities
The N3IWF supports the following UP functionalities:
Control Plane Procedures
Access to the 5GCN from the untrusted WLAN network mainly involves the following procedures:
Access Network Discovery and Selection
For discovery of the untrusted WLAN access network and the selection of N3IWF, the UE shall use the Access Network Discovery and Selection Policy (ANDSP). The ANDSP consists of WLAN Selection Policy (WLANSP) and non-3GPP access network (N3AN) node configuration information. The UE uses the WLANSP for selecting and connecting to the WLAN and is configured with a local IP address.
The UE uses the N3AN node configuration information for selecting a N3IWF. The N3AN information consists of a prioritized list of PLMNs including HPLMN and a PLMN that matches any PLMN the UE is connected to except the HPLMN. For each PLMN it includes a preference parameter indicating the preferred N3IWF in the PLMN and a FQDN parameter (Tracking/Location Area Identity or Operator Identifier) used to discover the address of N3IWF in the PLMN. The UE can also be configured with the N3IWF identifier configuration that includes the FQDN or IP address of the N3IWF in all PLMNS and shall prefer the same in the N3IWF selection independent of the preference parameter.
Registration, Authentication and Authorization
After the N3IWF selection, the UE proceeds with the registration, authentication and authorization procedures to access the 5GCN, as shown in Figure 7.
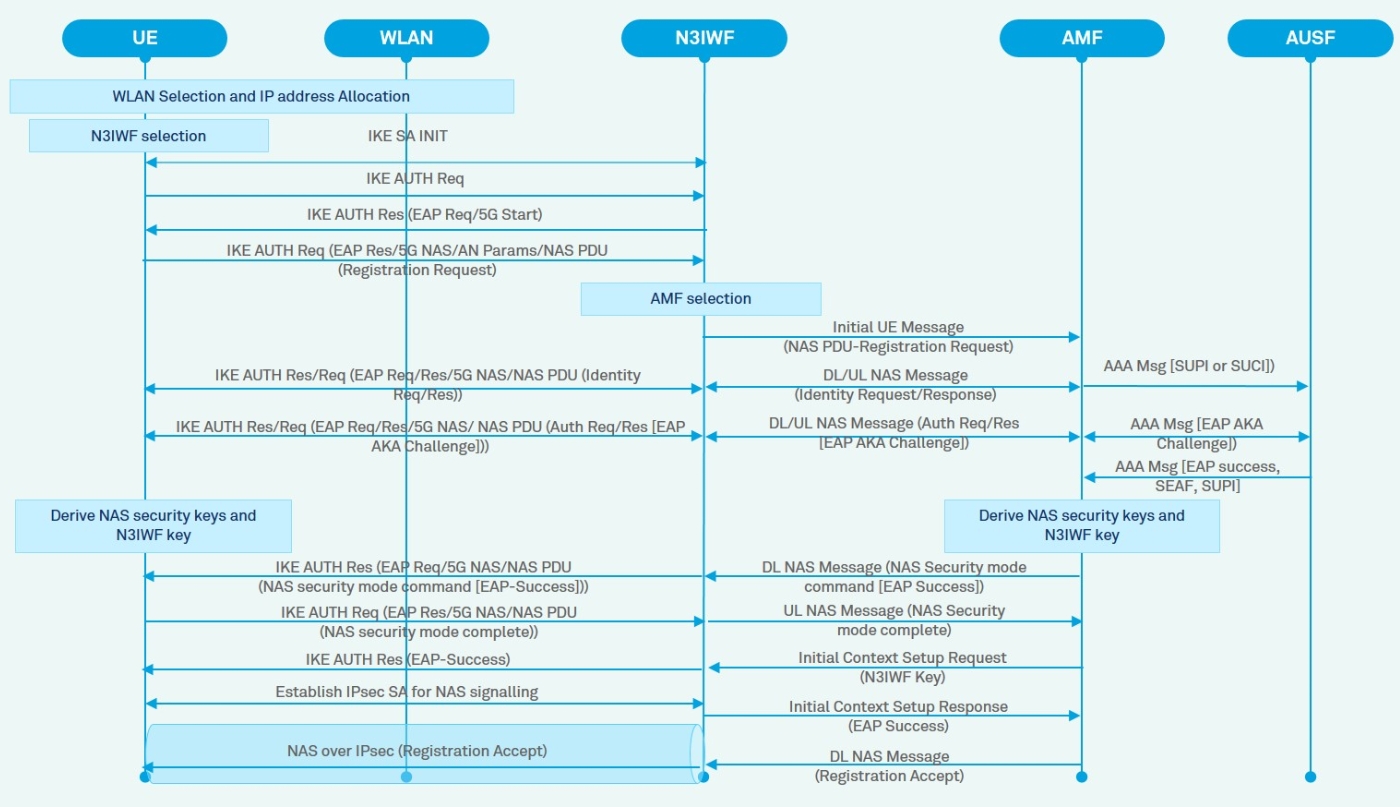
Figure 7: Registration Procedure
The registration, authentication and authorization procedures involve the following steps:
After registration, the UE shall support NAS signalling with 5GCN for mobility and session management functions using the N1 reference point. Multiple N1 instances shall exist for a UE connected to a 5GCN via 3GPP access and an untrusted WLAN. For a UE connected simultaneously to the same PLMN over a 3GPP access and an untrusted WLAN shall register with a single AMF with a common 5G-GUTI but the UDM manages independent UE Registration procedures for each access. For a UE served by different PLMNs, the UE is registered with two separate AMFs. For a UE registered with 5GCN over untrusted WLAN, a change of WLAN AP shall not lead the UE to perform a Registration procedure i.e. does not support mobility registration update in non-3GPP access
Registration Management (RM) and connection management (CM)
A UE that successfully registers to a 5GCN via untrusted WLAN transitions to RM-REGISTERED state for the non-3GPP access in the UE and the AMF. A UE with an active NWu connection (i.e., signalling IPsec SA) transitions to CM-CONNECTED state in the UE for non-3GPP access. A UE does not establish simultaneous NWu connections to access the 5GCN. The NWu connection is released as a result of an explicit deregistration procedure or either a WLAN release procedure or N3IWF release procedure which may be determined by the dead peer detection mechanism in IKEv2. The UE transitions to CM-IDLE state in the UE for non-3GPP access and starts the UE non-3GPP deregistration timer.
A UE with an active N2 connection between N3IWF and AMF transitions to CM-CONNECTED state in the AMF for non-3GPP access. The N2 connection is released either as a result of an explicit deregistration procedure or triggered by N3IWF as a result of NWu connection release. The UE transitions to CM-IDLE state in the AMF for non-3GPP access and starts the network non-3GPP deregistration timer. When the AMF releases the N2 interface, the N3IWF shall release all the resources associated with the UE including the non-3GPP Access Connection with the UE and its corresponding N3 resources.
A UE in CM-IDLE state over non-3GPP access performs service request procedure to request the re-establishment of the NAS signalling connection and the re-establishment of the user plane for some/all the PDU Sessions associated to non-3GPP access. A UE in CM-CONNECTED state over non-3GPP access performs either a UE initiated or network triggered service request procedure for the re-establishment of the user plane for the PDU Sessions associated to non-3GPP access.
A UE in RM-REGISTERED state in the UE/AMF transitions to RM-DEREGISTERED state as a result of an explicit deregistration procedure or deregistration performed on expiry of UE/network non-3GPP deregistration timer in the UE/AMF. Periodic registration update is not supported with untrusted WLAN.
When the UE is connected simultaneously over 3GPP access and untrusted WLAN the UE manages two RM and two CM states corresponding to each access independent of each other. When the UE is registered to the same PLMN the corresponding AMF also manages two RM and CM states for each access.
PDU Session Establishment
Figure 8 shows PDU session establishment for a UE accessing the 5GCN through the untrusted WLAN.
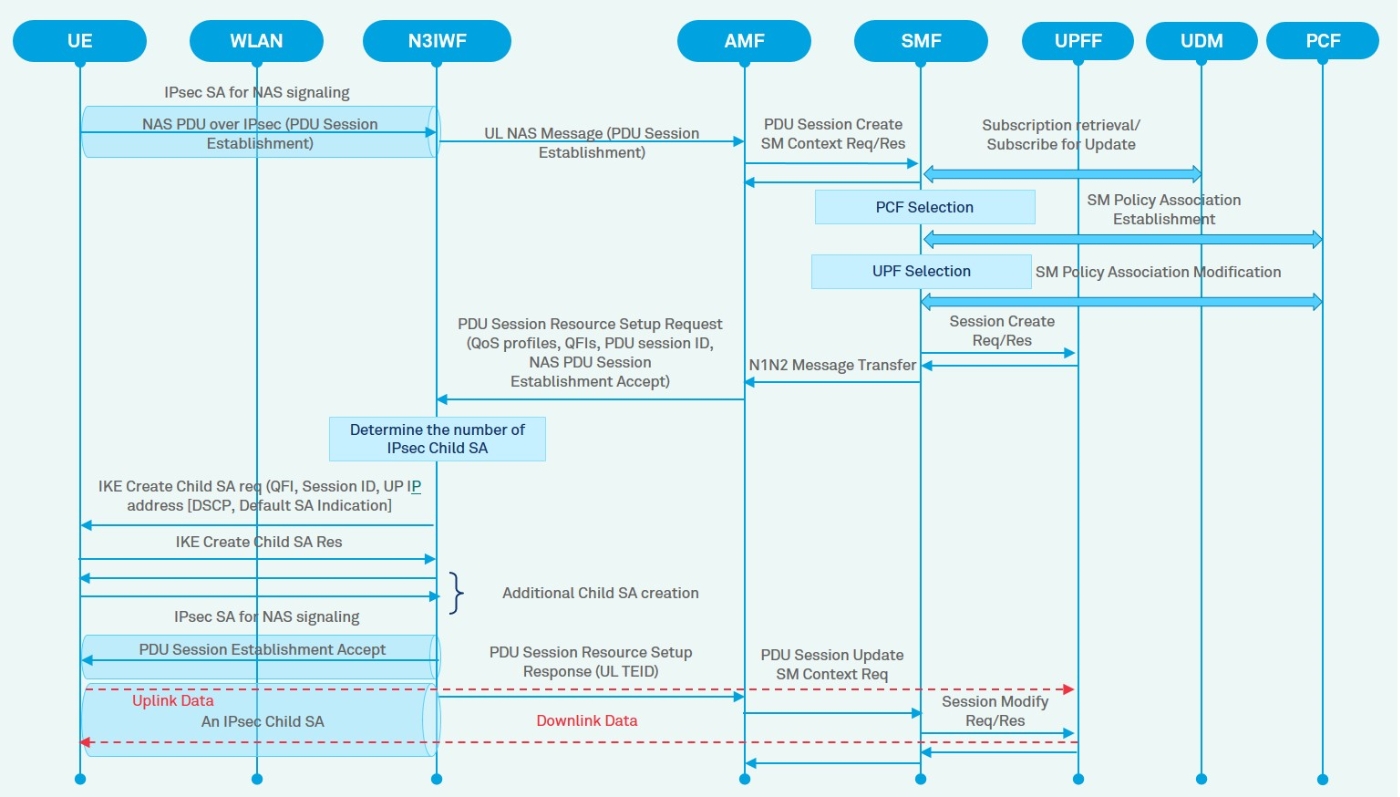
Figure 8: Session Establishment Procedure
The PDU session establishment procedure involves the following steps:
PDU sessions over the 3GPP access may be served by SMFs different from the SMF serving the PDU sessions over the non-3GPP access.
PDU session deactivation
The deactivation of the UP connection of an existing PDU session causes the corresponding NWu connection (i.e., IPsec Child SAs and N3 tunnel) to be deactivated. The UP connection of different PDU sessions can be deactivated independently when a UE is in CM-CONNECTED state. If a PDU session is an always-on PDU session, the SMF should not deactivate a UP connection of this PDU session due to inactivity. Release of PDU Sessions over the non-3GPP access does not imply the release of N2 connection.
Paging is not supported with untrusted WLAN. Hence when the AMF receives a message corresponding to a PDU session for a UE in CM-IDLE state for non-3GPP access, a network triggered service request procedure may be performed over 3GPP access irrespective of UE state for 3GPP access. A network triggered Service Request procedure over non-3GPP access may also be performed for a UE in CM-IDLE state for 3GPP access and CM-CONNECTED state for Non-3GPP access in AMF when paging over 3GPP access is not performed.
Multiple PDU Sessions over 3GPP and non-3GPP access
A UE registered simultaneously over a 3GPP access and an untrusted WLAN may have multiple PDU sessions over both the access with each PDU session active in only one of the access. When the UE transitions to CM-IDLE in either of the access the UE may move the PDU Sessions in the corresponding access to the target access based on UE policies. The UE may need to initiate a registration procedure in the target access for the handover and then initiates the PDU session establishment with the PDU session IDs of the PDU sessions moved. The core network maintains the PDU Sessions but deactivates the N3 user plane connection for such PDU Sessions. Based on the implementation the UE may initiate a Deregistration procedure in the access that has no PDU Sessions.
Multi-Access PDU Session
3GPP Release 16 supports Access Traffic Steering, switching and splitting (ATSSS) that allows a ,multi-access PDU session where a PDU session with multiple packet flows may select 3GPP access or untrusted WLAN for each packet flow or a packet flow may be switched between 3GPP access and untrusted WLAN or a packet flow can be split across 3GPP access and untrusted WLAN. The PDU session establishment procedure contains additional information and user plane establishment to achieve the same.
User Plane
After the completion of PDU session establishment and user plane IPsec Child SAs are established between the UE and N3IWF, the UE can send uplink and downlink traffic for the session with various QoS flows over the untrusted WLAN network using the established IPsec Child SAs and the associated GTPU tunnel between the N3IWF and UPF.
Uplink Traffic
When the UE must transmit a UL PDU, it shall determine the QFI associated with the PDU using the QoS rules of the corresponding PDU session and shall encapsulate the PDU inside a GRE packet with the QFI value in the header of the GRE packet. The UE shall forward the GRE packet to N3IWF via the IPsec Child SA associated with the QFI by encapsulating the GRE packet into an IPsec packet in tunnel mode with source address as UE IP address and destination address as UP IP address associated with the Child SA.
When the N3IWF receives the UL PDU, it shall decapsulate the IPsec header and GRE header and determine the GTPU tunnel ID corresponding to the PDU session. The N3IWF shall encapsulate the UL PDU inside a GTPU packet with the QFI value in the header of the GTPY packet and shall forward the GTPU packet to the UPF via N3.
Downlink Traffic
When the N3IWF receives a DL PDU via N3 from the UPF, the N3IWF shall decapsulate the GTPU header and use the QFI and the identity of the PDU session in the GTPU header to determine the IPsec Child SA to use for sending the DL PDU over NWu to the UE.
The N3IWF shall encapsulate the DL PDU inside a GRE packet with the QFI value in the header of the GRE packet. The N3IWF may also include a Reflective QoS Indicator (RQI) in the GRE header which shall be used by the UE to enable reflective QoS. The N3IWF shall forward the GRE packet with DL PDU to the UE via the IPsec Child SA associated with the QFI by encapsulating the GRE packet into an IP packet in tunnel mode with source address as the UP IP address associated with the Child SA and destination address as the address of the UE.
QoS
For a UE accessing the 5GCN through the untrusted WLAN, the N3IWF supports QoS differentiation and mapping of QoS flows to non-3GPP access resources. A QoS flow is controlled by the SMF and can be preconfigured or established via the UE requested PDU session establishment or modification procedure. The N3IWF shall determine the number of user plane IPsec Child SAs to establish and the QoS profiles associated with each Child SA based on local policies, configuration and the QoS profiles received from the network. The N3IWF shall then initiate IPsec SA creation procedure towards the UE to establish Child SAs associating to the QoS flows of the PDU session. The QoS functionalities of the UE, N3IWF and UPF are specified in Figure 9.
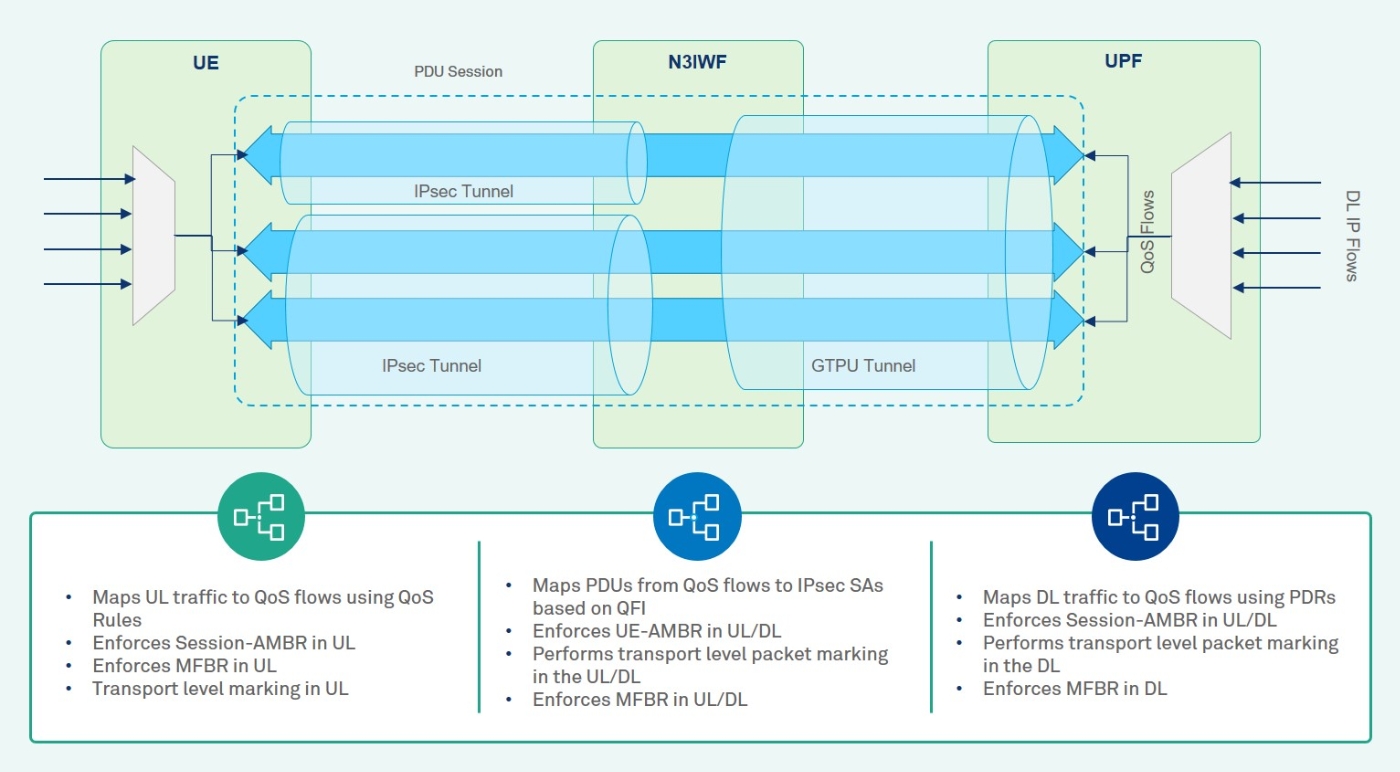
Figure 9: QoS for Untrusted WLAN Accessing 5GCN
Summary
The untrusted non-3GPP access which basically corresponds to WLAN interworking with 5GCN is provided through a N3IWF. However, unlike the earlier architectures where the WLAN interworking network element (PDG/ePDG) was part of the 3GPP core network the N3IWF acts as an access network similar to the 3GPP access. This allows common procedures in both 3GPP access and non-3GPP access for registration, authentication and session handling. Paging, mobility registration and periodic registration are not supported with untrusted WLAN. Multiple PDU sessions can be established over both the 3GPP access and the untrusted WLAN and the PDU sessions can be transitioned between them. Further a multi access PDU session may be established over 3GPP access and untrusted WLAN with support for ATSSS.
References
1 3GPP TS 23.501: "System Architecture for the 5G System; Stage 2"
2 3GPP TS 23.502: "Procedures for the 5G System; Stage 2"
3 3GPP TS 24.501: "Non-Access-Stratum (NAS) protocol for 5G System (5GS); Stage 3"
4 3GPP TS 24.502: "Access to the 3GPP 5G Core Network (5GCN) via Non-3GPP Access Networks (N3AN); Stage 3"
5 3GPP TS 38.413: "NG-RAN; NG Application Protocol (NGAP)"
6 3GPP TS 23.402: "Architecture enhancements for non-3GPP accesses".
7 3GPP TS 23.234: "3GPP System to Wireless Local Area Network (WLAN) Interworking; System Description".
8 3GPP TS 33.501: "Security Architecture and Procedures for 5G System".
Abbreviations
5GCN 5G Core Network
AKA Authentication and Key Agreement
AMBR Aggregate Maximum Bit Rate
AMF Access and Mobility Management Function
ANDSP Access Network Discovery and Selection Policy
ATSSS Access Traffic Steering, Switching and Splitting
AUSF Authentication Server Function
CM Connection Management
CP Control Plane
DL Downlink
EAP Extensible Authentication Protocol
ePDG Evolved Packet Data Gateway
GGSN Gateway GPRS Support Node
GRE Generic Routing Encapsulation
GTPC GPRS Tunnel Protocol Control Plane
GTPU GPRS Tunneling Protocol User plane
GUAMI Globally Unique AMF Identifier
IKE Internet Key Exchange
IPsec IP Security
NAS Non-Access Stratum
N3IWF Non-3GPP Inter Working Function
NGAP Next Generation Application Protocol
N3AN Non-3GPP Access Network
PDG Packet Data Gateway
PLMN Public Land Mobile Network
PMIP Proxy Mobile IP
QFI QoS Flow Identifier
QoS Quality of Service
RM Registration Management
RQI Reflective QoS Indicator
SA Security Association
SCTP Stream Control Transmission Protocol
SMF Session Management Function
TTG Tunnel termination Gateway
UDM Unified Data Management
UE User Equipment
UP User Plane
UPF User Plane Function
WAG Wireless Access Gateway
WLAN Wireless LAN Access NetworkWLANSP WLAN Selection Policy