Traditionally, security infrastructure and components are managed using a hierarchical support model, with engineers and service desk team performing pre-defined set of activities. They are responsible for the upkeep of the infrastructure, management of the devices, handling of service requests, and reporting of service status as part of regular review with the stakeholders.
Various commercial tools and platforms are used to help in the operations. These are tools to monitor device availability or performance, scripts to automate generic tasks, along with service management platforms for ticket and workflow management in the operations process.
With the increase in the number of security products and the associated complexity, enterprises and service providers have started using orchestrators and compliance management tools to reduce the effort of managing these products, and to improve compliance of the infrastructure.
Despite the presence of these security tools and technologies, enterprises face cyber-attacks, and malware infections.
The main reason for the security gap is missing “security hygiene” of the infrastructure and limited visibility of infrastructure and associated service effectiveness.
A proactive and cohesive approach to security
Effective security service requires standardized infrastructure and components. It also stipulates the use of a platform that can provide the required set of services, yet be flexible enough to cater to any new or complex requirement. Hence, the concept of productized services is highly effective in ensuring service effectiveness and filling the gaps in traditional security operations.
Wipro’s state-of-the-art Security Management Center (SMC), built on the principle of “Beat Before Beaten”, has an integrated approach combining Predictive, Preventive and Proactive activities based on automation and analytics, which ensures a 360-degree business-oriented view of security operations and thus,
SMC is a purpose-built security operations and orchestration product to help deliver managed security services. It offers operational insights, prioritization of risks, pre-integrated tools, short deployment time, reusable use cases, etc. to help enterprises attain operational maturity, thereby greatly reducing time-to-market.
Its unique proactive approach to provide insights into the security infrastructure gives organizations visibility into their security posture. Wipro uses Security Management Center to visualize the security infrastructure, holistically to view its customer’s security posture.
The consolidated view comprises of risk, reliability and efficiency posture of the infrastructure. It delivers the richness of correlated data, aggregated information, and transparency related to the offered services.
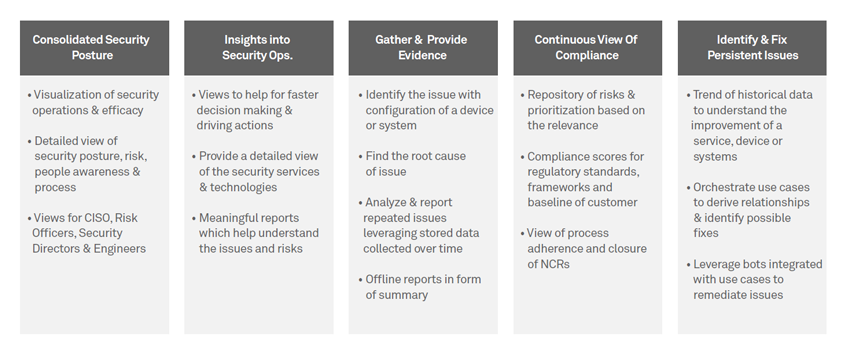
Figure 1: Effective security operations with Security Management Center
SMC provides a unified view translating individual tool views/ reports into meaningful dashboards to stakeholders within the enterprise hierarchy. For instance, an executive view for the CISO shows whether any risks are manifesting due to ineffective or inconsistent application of security controls or if configurations are not meeting the baselines. Similarly, it provides an operational view to Operations Manager and a technology view to Analysts and Engineers.
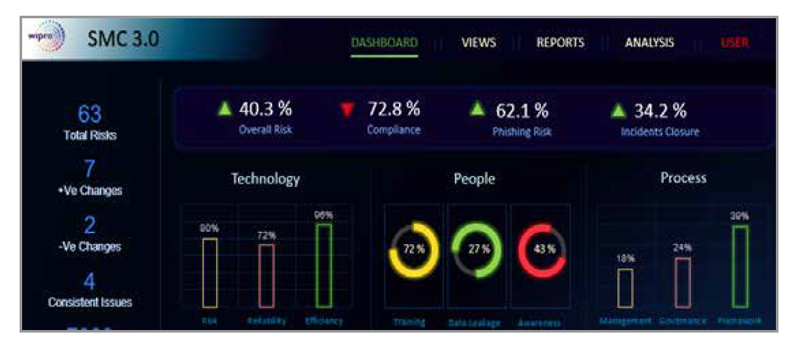
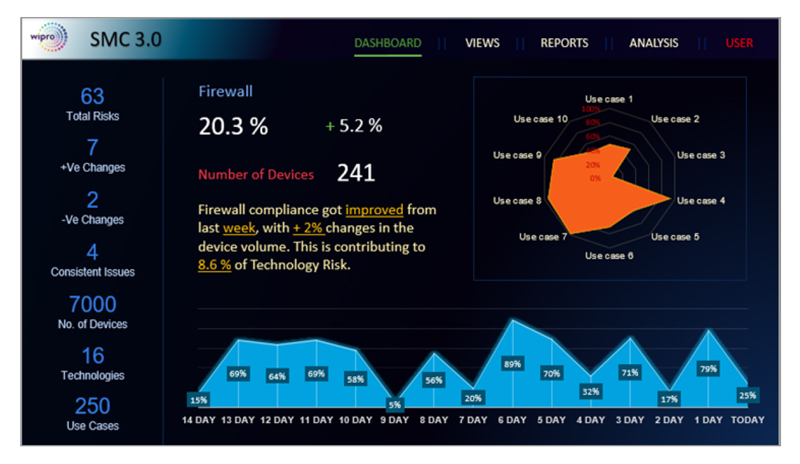
Figure 2: Snapshots of Security Management Center dashboards
Security Management Center: Ensuring integrated visibility
SMC service architecture consists of multiple tools, collector and different data access methods using which the data is captured, correlated and aggregated to create the required views in the portal.
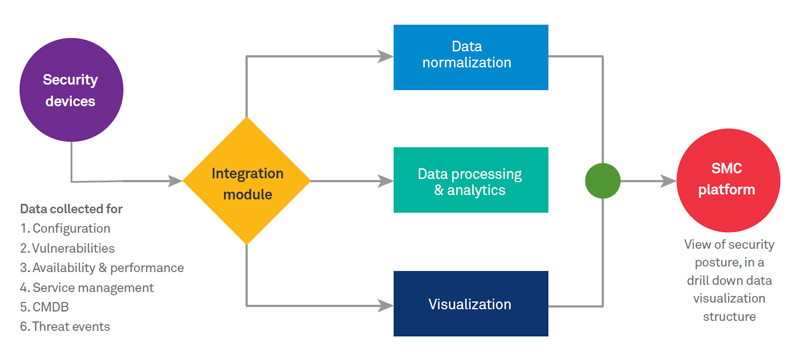
Figure 3: Indicative diagram for SMC data flow
The architecture consists of a server hosting SMC platform with the data collection module, with IP connectivity to various security devices available in the infrastructure. The configuration of these security devices, are assessed using set of use cases defined as the baseline criteria. These use cases are derived from security frameworks, regulatory standards, vendor best practices and Wipro’s experience. SMC integrates with these security devices using APIs to collect the required information.
The vulnerability management tool deployed at customer infrastructure is integrated to collect relevant information defined by pre-defined use cases. SMC integrates with orchestrator tools deployed at the customer’s premise, which integrates with the firewall, load balancer devices to collect the configuration and rule bases, and access Firewall logs to analyze and create meta data content. The meta data is then sent to management server for further analysis. The service management tool hosted at customer data center is integrated with SMC using supported mechanisms and collect security operations ticket data in pre-defined time interval.
The health monitoring tool is hosted in the data center, which monitors the infrastructure security devices including firewall, load balancer, forward proxy, end point security management servers, etc. to collect health and performance related data, for analysis and reporting to SMC. The data gathered from all the above processes are then sent to the database of SMC platform, where it is further correlated and aggregated, to provide integrated visibility towards security infrastructure and security posture. SMC portal shows consolidated view of security posture as operational risk, efficiency and reliability view, with the capability to drill down to individual device status.
Angshuman Chattopadhyay
Infrastructure Security within Cybersecurity and Risk Services, Wipro
Angshuman Chattopadhyay is the Consulting & Solutions Lead for Infrastructure Security within Cybersecurity and Risk Services at Wipro. He brings extensive experience with over 19 years in IT and cybersecurity across a wide range of global roles.
Angshuman can be reached at angshuman.chattopadhyay1@wipro.com