Cloud adoption & common security challenges
Industries are adopting cloud for various benefits. Some of the key driving factors are:
Cloud benefits are being realized everywhere today. However, it also brings some security challenges to enterprises: they have to protect their “crown jewels” data from various sophisticated advanced threats.
As per an old school of thought, cloud is insecure, and on-premise-centric solutions are cheaper. This is far from the truth: comprehensive threat visibility and protection to the hybrid/multi-cloud assets and continuous compliance validations can be achieved through unified and integrated security solutions that are designed for public cloud.
Many organizations have adopted a cloud-first strategy and try to eliminate on-premise footprint for their applications and infrastructure. However, many legacy applications demand on premise setup due to dependencies, and add complexity and inefficiencies through multiple security solutions for hybrid environments.
Highly regulated industries like Banking/Insurance meet compliances likes PCI & GDPR. Their cloud service providers (CSPs) natively support the highest privacy controls and the ability to continuously assess their cloud workloads and applications against compliance standards, and alert the enterprises for the gaps with recommendations. Some countries’ (like UAE) laws mandate to keep sensitive data within their regions, and CSPs like Azure provide Geo locations to keep the data within their boundaries to achieve compliance.
One of the key concerns most enterprises have today is “Availability” of their cloud services. In the initial days of cloud adoption, confidentiality and compliance/governance were primary concerns, but with the CSPs’ advancing maturity over time, they are no longer a cause of concern. However, now, enterprises are heavily dependent on cloud services for their mission and business-critical applications.
Visibility to all cloud workload resources is critical to apply security and compliance policies. In a hybrid and multi-cloud environment, bringing all security alerts to a centralized and modern SIEM platform powered with Extended Detection and Response (XDR) helps in effective monitoring, investigation, threat hunting and incidents response.
How you can address these challenges
Microsoft provides a comprehensive and integrated security and compliance solution for Azure cloud workloads. Its layered security helps in achieving Defense in Depth strategy. Most of these native controls can be extended to hybrid and multi-cloud environments
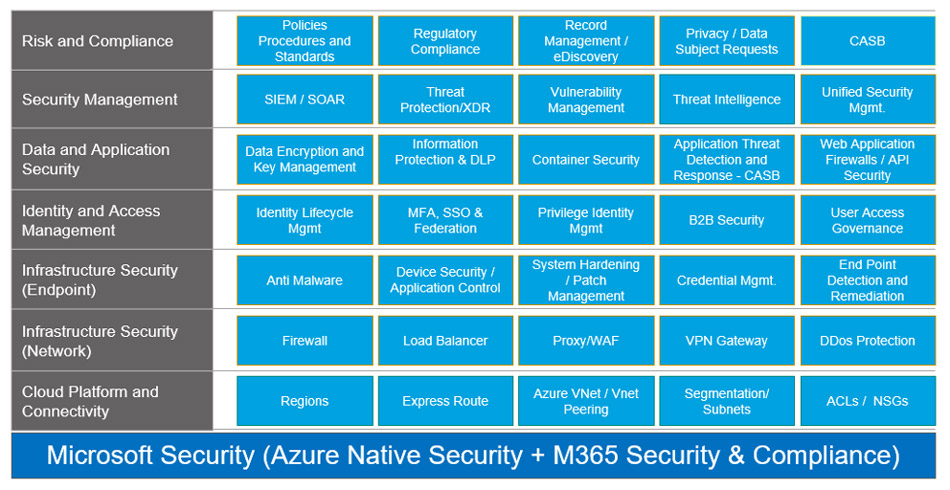
Figure 1 – Microsoft Native controls for intelligent & integrated layered security
Securing the cloud data is #1 priority
Enterprises have more control when the data resides within the network perimeter. With cloud adoption, data is stored and processed by many 3rd parties like CSPs and SaaS providers. Though certain level of data security and assurance is provided by these 3rd party providers, it is the enterprise’s responsibility to ensure adequate data protection controls to maintain confidentiality, integrity and availability.
Encryption at all levels is essential to build a persistent data security strategy for the enterprise. While enterprises need to keep their data on premise or with one specific CSP, key management and protection becomes critical.
Azure provides a Key Vault service that can be leveraged to a hybrid and multi-cloud environment through Azure Arc, and supports bring your own key (BYOK) and 3rd party HSMs to protect your master keys. There are concerns that CSPs can get access to customer keys. But, there are many controls available to limit the access to the keys and get visibility to who has accessed the keys for compliance perspective.
Enterprises dealing with most sensitive data that demands strictest protection requirements can leverage Microsoft Double key encryption (DKE). In this approach, customer holds one key with full control and Microsoft stores one key.
Customers who move their workloads and data to Azure cloud get greater confidence as Microsoft provides a holistic solution to secure organization’s sensitive data.
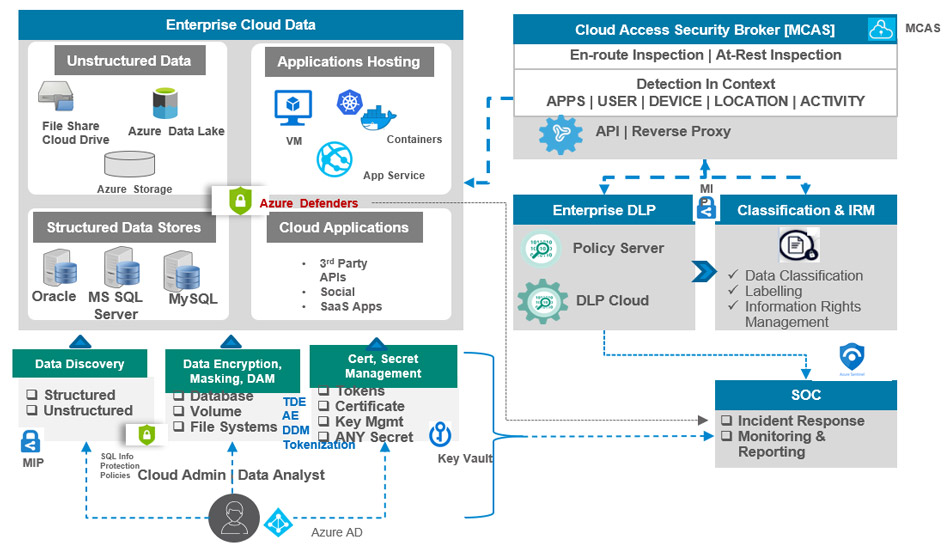
Figure 2: Integrated data security controls from Microsoft
IAM strategy is key to success
Identity and Access Management plays an important role in protecting enterprise users and the applications that are deployed on premises and in cloud. Enterprises leverage CSPs and 3rd party IAM vendor solutions to provide identity lifecycle and access functions for regular, privilege users and system accounts. IAM availability is critical and higher availability assurance from providers like Azure AD (99.99%) ensures business continuity. When enterprises are dealing with multi-cloud environments, privilege identity and access are given highest priority to ensure least privilege principles are in-place.
A centralized IAM solution to manage identity and access in a hybrid and multi-cloud environment helps to reduce the complexity and improve the efficiencies. To mitigate privilege escalation attacks, enterprises need to continuously monitor the privilege users’ activities, their role/permission utilization, and build a process to remove unused and excessive privileges frequently.
Since COVID-19, enterprises are witnessing increased phishing and identity-centric attacks. Risk-aware authentication with real-time protection is essential these days for users connecting through internet. Most enterprises leverage Azure AD Identity Protection that detects real-time user and session risks and provides various mitigation methods like blocking access or enforcing password reset etc.
Microsoft Azure AD helps organizations to adopt single identity approach to provide unified IAM policies across hybrid and multi-cloud environments for B2E/B2B/B2C identities. Azure AD conditional access with identity protection ensures zero trust access for users who access enterprise applications.
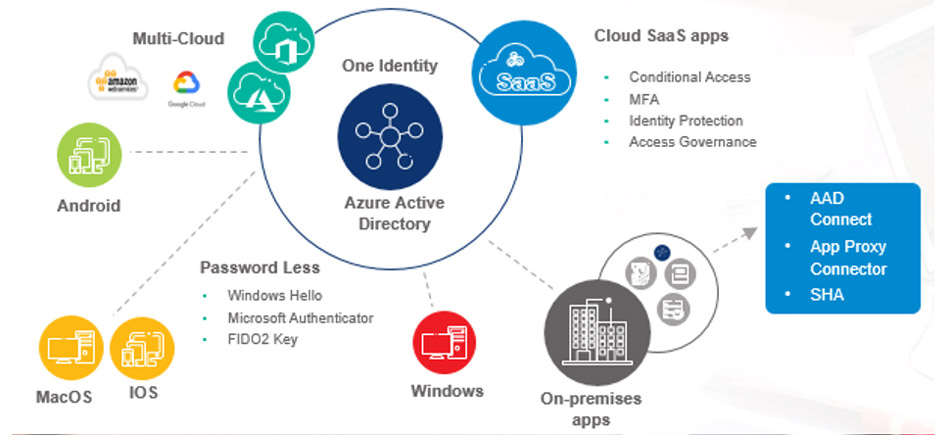
Figure 3: Single identity strategy for hybrid and multi-cloud
Active Directory has been the heart of identity trust for most organizations until now. This is a two-decade old technology designed for on-premise network and systems, but being extended to support cloud workloads. Most of the attacks are targeted to gain control on the enterprise Active directory. Reducing the dependency on Active Directory is one quick ways of reducing the risk. For example, adopting cloud-based authentications for workstations in the form of “cloud joined” devices with strong authentication will greatly reduce the AD exposure to identity related risks. Decentralized passwords through password-less adoption can also reduce various password-related attacks towards Active Directory. Also, cloud workloads that require active directory can leverage CSP managed services like Azure AD Domain Service for reduced complexity and increased security.
Unified cloud security posture management and workload protection
In a single or multi-cloud environment, continuously monitoring the security and compliance posture, and rapidly detecting and responding to the threats are critical to success. Cloud security posture management (CSPM) solutions help to achieve this. CSPs Native Cloud Security solutions like Azure Security Center offers unified and integrated CSPM functions for hybrid and multi-cloud environments. Securing the workloads, VMs, containers and server-less functions are also critical and cloud workload protection platforms (CWPP) help to achieve this.
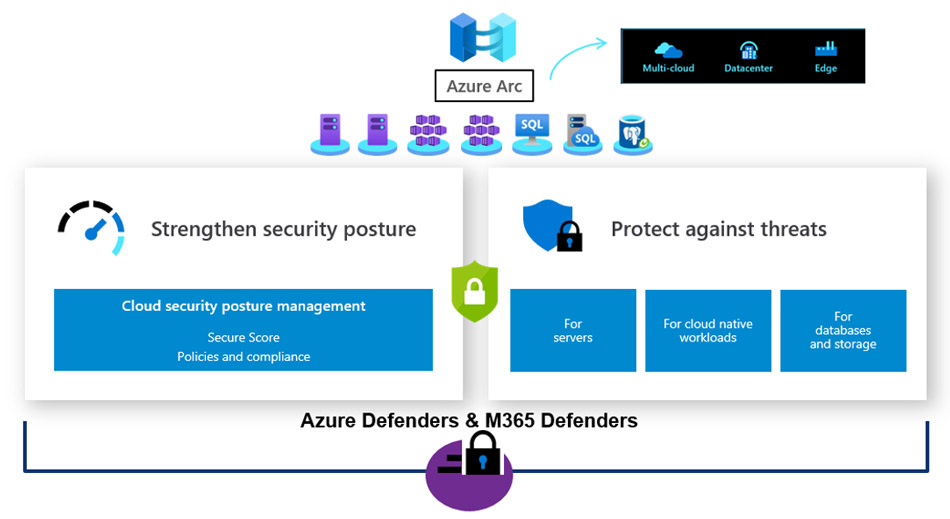
Azure Defenders provide an integrated security to cover all azure workloads and can be extended to hybrid and multi-cloud environments. Multiple non-CSP/3rd party solutions are also available that provide both CSPM and CWPP for multi-cloud environments.
In conclusion
To summarize, common security challenges in a hybrid and multi-cloud environments are:
Enterprises can mitigate these challenges by:
Wipro and Microsoft, together, bring a strong portfolio of solutions and services to help you overcome security and compliance challenges in a hybrid/multi-cloud environment. For details, connect with us here.
Prakash Narayanamoorthy
Partner & Microsoft Security Principal Architect at Wipro
Prakash has over 19 years of experience in the Identity and Security domain, helping multiple large global organizations with their cloud security and compliance transformation. He was one of the presenters from Wipro at this CISOs panel event.