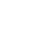Recent data breaches have highlighted a common vulnerability — third-party cloud platforms, where hackers have accessed millions of sensitive customer records. Even though the breaches were carried out by different adversaries, they shared a common thread — the involvement of third-party cloud services.
Robust risk management can protect your organization
As businesses increasingly rely on third-party providers for essential services, it's crucial to assess and manage the associated risks.
A robust Third-Party Risk Management (TPRM) program is vital for mitigating the risk of third-party breaches. The program should verify that vendors both adhere to the organization’s security standards and comply with regulatory requirements. TPRM must encompass the entire lifecycle of a third-party engagement, including onboarding, mitigation of risks, and continuous monitoring.
Wipro has compiled the following best practices that can help safeguard your organization:
1. Minimize third-party access to sensitive data: Implement Privileged Access Management (PAM) to restrict third-party access to only what is necessary for contractual obligations. Establish clear policies for data storage and transfer.
2. Create an incident response plan: Your plan should outline security incident protocols and include provisions for third parties to promptly notify your organization if a breach occurs.
3. Incorporate risk management into contracts: Use detailed contractual agreements that specify security requirements, responsibilities and expectations to ensure vendor accountability.
4. Use data intelligence tools: Utilize tools to assess the cybersecurity posture of your vendors. Continuous monitoring of information security, vulnerabilities, and threats supports informed risk management decisions and minimizes attack impacts.
5. Offer training and awareness programs for employees and third parties: Ongoing education helps everyone understand their roles in protecting data and identifying potential risks.
6. Ensure compliance and regulatory adherence: Your third-party vendors should comply with relevant industry standards like GDPR and HIPAA. For critical vendors with access to highly sensitive data, request that they maintain security certifications or submit to annual assessments such as ISO27001, CSA STAR, PCI DSS, NIST, SOC 2 Type 2, and ISO 23001.