Organizations that use cloud computing have long had concerns about security. Those concerns have only increased as enterprises embrace more-significant use of containers in production. Data protection, in particular, is now front and center in every company’s IT strategy, especially when sensitive and proprietary data required by the application moves outside the organization – such as in the cloud. In these scenarios, it becomes more critical to protect that data in-use. Hence, the rise of confidential computing, an emerging trend that focuses on securing data in-use.
Confidential computing adds a layer of protection to data and code by enabling private encryption, increased privacy, and protection of intellectual property. The concept has long existed in various forms of intellectual property protection with support for custom hardware. With the evolution of cloud and hardware, the combination has made confidential computing available in public clouds. And that is good, because it is critical for protecting data in the cloud.
Confidential computing has many benefits and uses that pertain to protecting data in trusted environments. For one, better cloud data security means not even cloud providers can see their customers’ data, even if cloud administrators or malicious hackers have exploited kernel bugs in hosts. Cloud customers have authority over their data and processing at all times including while in use. Processing in-memory with encryption for data and code limits access to provide the most protection for cloud data.
Confidential computing also enables end-to-end security encryption that protects data while in the state of being processed or in use. For the safety of data like financial information, encryption keys are used for highly sensitive and confidential data. Greater transparency is available when moving data between environments, especially involving transformational computing, and standard confidential computing application solutions can be developed and moved across different cloud platforms. In addition, it protects data from malicious and insider threats and is data compliant with General Data Protection Regulations (GDPR).
Data Protection
Why is data protection so important and relevant now? The rapid adoption of the cloud offers cost advantages and infrastructure agility, driving enterprises across industries to migrate their workloads to the cloud. The initial journey with non-critical applications has been successful. But when it comes to moving core services – using confidential data – to the public cloud, domain data-protection concerns persist. Confidential computing in the cloud is the game changer that brings the trust that is necessary to fully embrace the cloud at large scale.
In the cloud, the data lifecycle has three stages, each with different levels of treatment required to encrypt data for security. Data at rest is information stored in a hard drive, file server, database, etc. Data in transit is information that travels through email, HTTP, instant messaging, or any other type of public or private communication. And data in-use is information that is opened and consumed by an application or accessed by users.
While data security is well established for at rest and in transit stages, in-use has been left with de-identification and homomorphic encryptions that only provide partial protection. Confidential computing addresses this gap with a new framework and design in coordination with the Confidential Computing Consortium (CCC).
Confidential Computing Consortium
The confidential computing concept is the brainchild of Confidential Computing Consortium, a group of organizations made up of hardware vendors, cloud providers, and developers such as Microsoft, Intel, and Google. The consortium has a common goal of building tools supporting the protection of data. The solution is focused around software- and hardware-based security, extending traditional data encryption at rest and in transit to in-compute. The encrypted in-compute solution protects against risks of malicious insiders, network vulnerabilities for hardware, or software-based technology that could be compromised.
The original concept that needed custom hardware has been enhanced for the cloud. The intent is building cross-platform tools for confidential computing in an effort to make it easier to run computations in enclaves – a trusted execution environment (TEE) projected from hardware, OS, and other applications.
How Confidential Computing Works
Typical modern applications focus on data security at rest and in transit with encryption, leaving a gap of data protection for data in use. Confidential computing focuses on securing data while in use mainly when data is processed in-memory. The intent is to allow data to be processed in-memory while the data is still encrypted (to the world outside memory). This reduces the exposure of any sensitive data. The only time data is unencrypted is when code on the system allows a user to access it. This is done to explicitly ensure that at no point can a cloud service provider have access to any customer data. The exclusion includes administrators of the machine and database. This layer of security provides complete trust for execution in the enclave or TEE.
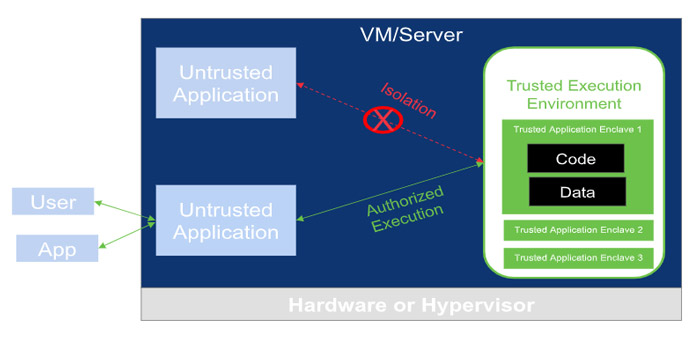
Figure 1: Trusted Execution Environment (TEE) Application Architecture
Hardware-based TEE
The protection of data-in use through isolated in-memory computing is achieved by hardware-based TEE. The hardware-based memory protection provides a higher degree of control and transparency for sensitive data to be exposed while in use. The hardware technology has evolved from cloud to edge as organizations using cloud services need protection controls to help safeguard sensitive data in use at runtime wherever it is deployed.
Tools and Services
Organizations that are part of CCC have developed tools supporting the development of trusted computing applications. These applications can run in enclaves or TEE adhering to confidential computing standards.
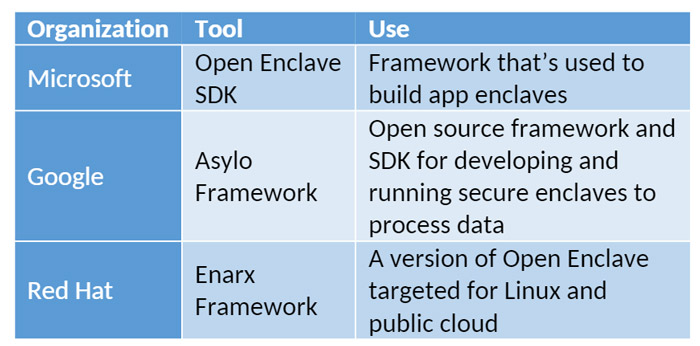
Figure 2: Vendor Solutions for Enclaves
Cross-Industry Collaboration
The CCC established industry efforts to advance computational trust and security of next-gen cloud and edge computing. By bringing together hardware vendors, cloud providers, software developers, and system integrators, the consortium was able to accelerate the adoption of TEE technologies and standards.
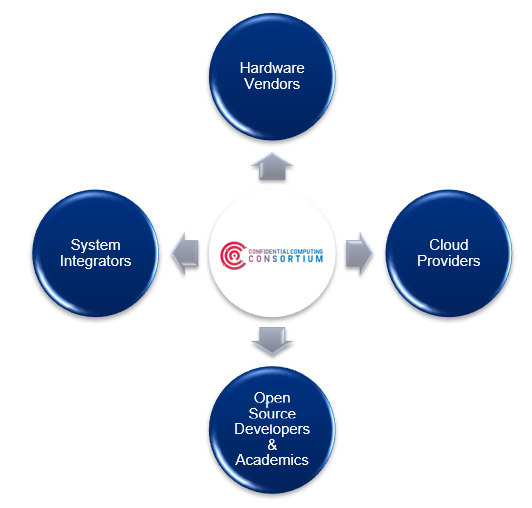
Figure 3: Confidential Computing Cross-Industry Collaboration
Confidential computing is fast evolving as a natural fit for the increasing use of cloud services to provide data security and privacy with increased transparency. The framework has a lot to offer, and as it matures, the use of edge computing will benefit the most, enabling innovative solutions addressing data security concerns.
Bala Kalavala
Chief Architect, Distinguished Senior Member Technical Staff (DMTS), Wipro iDEAS
Bala Kalavala is a pragmatic technology enthusiast with 20 years of modern software design experience for cross-industry digital transformations. Currently he heads the Americas Enterprise Architecture for iDEAS in Wipro as Chief Architect. Bala’s outcome driven thought leadership in solutions cross pollinates from his experience in a variety of industries and enterprise platforms.